Uni·Secure
Vulnerability Detection and Response
Prioritize continuous vulnerability detection and response (VMDR) to help secure your IT & cybersecurity environment
Overview
Even the best security strategy is defeated by the weakest link in your organization. Uni·Secure Vulnerability Detection Response powered by Qualys establishes the cyber security foundation that today’s hybrid, dynamic, and distributed IT environments require. It is a continuously orchestrated workflow cycle, consisting of automated asset discovery, vulnerability management, threat prioritization, incident response, and optional remediation. By adopting the Uni·Secure VDR lifecycle, organizations decrease their risk of compromise by effectively preventing breaches and quickly responding to threats through a vulnerability management program.
Real-Time, Deep Visibility, Powerful Scanning
Everything visible, everything secure. Uni·Secure VDR gives you a continuous, always-on analysis of your global hybrid-IT, security, and compliance posture, with visibility across all your IT assets, wherever they reside. With automated, built-in threat prioritization and response capabilities, Uni·Secure VDR is a complete, end-to-end security solution.
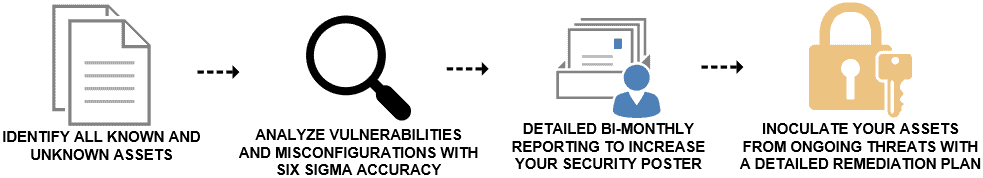
Identify vulnerabilities that have the most impact on your risk exposure with recommendations.
Deep visibility into your growing IT systems including on-premises, remote, and cloud-based assets.
Asset discovery, inventory and categorization of all known and unknown assets for easy review.
Detailed reporting increases the security of your organization by identifying the vulnerable areas
Compliance scanning to satisfy requirements for mandates such as PCI, CIS, or general cyber insurance.
Want to Learn More?
Threat Identification and Prioritization
Threat identification using continuous threat intelligence and vulnerability assessments to take control of the evolving threat landscape and to alert you when network anomalies are detected. Threat identification is an important part of any security strategy. It involves using continuous threat intelligence and vulnerability assessments to detect and identify potential threats before they can cause damage. By identifying potential threats early, organizations can take proactive measures to mitigate the risks associated with them. Additionally, threat identification also enables organizations to develop effective strategies to respond quickly and effectively when a malicious attack occurs.
Patch Detection and Management
Automatic correlation of vulnerabilities and patches helps to decrease remediation response time. Search for CVEs to identify the latest superseding patches for rapid resolution.
Vulnerability Management
Continuous detection of software vulnerabilities with the most comprehensive signature database ranging across the widest category of assets.
An Expert Security Team
World-class vulnerability management experts provide expert guidance and support with a goal of continuous evaluation and vulnerability containment. By ensuring that the right processes are being followed and that appropriate measures are taken in response to vulnerabilities as they arise, organizations can rest assured that they are taking all necessary steps to protect their systems from malicious actors.




